The cryptography system described above was developed in 1918 by the cryptologist G. Vernam and called the "One-Time-Pad": The key code is generated and only written down on two pads for Alice and Bob. Each page with the code can only be used once. In times of the Cold War, the key codes were printed on small pads and sent on by messengers. If the messenger did not arrive at his destination, the "enemy" had only got hold of the key code. As this code had nothing to do with the real message, it was of no value to the "enemy". The real message was then encoded with a different code. The obvious danger of this method lies in the possibility that the code could be copied unnoticed by the messenger while he was on his way. If and when that happened, the encoded message could be decoded.
The One-Time-Pad system is 100% secure [Sha49], if the following requirements concerning the key code are met::
-
Requirement 1: The code must only be used once.
-
Requirement 2: The code must be at least the same length as the real message.
-
Requirement 3: The code must be chosen unpredictably at random
-
Requirement 4: The code must be known to no more than two persons.
Which requirements can be met so far?
For
requirement 1, the sender and the receiver are equally responsible.
Each key code must be destroyed immediately after one-time use so that it
cannot be used again. Requirement 2 can be complied with by the sender.
He must only encode a message if he has sufficient code bits at his
disposal.
For Requirement 3, random numbers are needed in
order to generate the code. Random numbers can e. g. be created with
the help of a computer. This computer randomness is, however, generated via
a calculation. The basis for this calculation is a start value which recurs
infrequently. The "randomness" of the computer figure therefore only
depends on the complexity of the calculation rule and on the start
value. Computer-generated random numbers are therefore called "pseudo
random" and are not suitable for the completely random generation of a
code.
Real random numbers can be generated with
the aid of quantum physics. If a single photon hits a beam splitter, it
is either reflected (binary 1) or transmitted (binary 0) completely
at random
(pic. 1). There is no mathematical rule behind this process. Such a
quantum random generator is described in detail with experiments in the
chapter Quantum random.
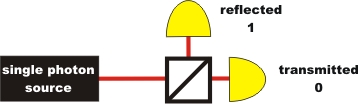
pic. 1: quantum random generator with announced single photon source
With the quantum random generator, requirement 3 can be met. Now, the random generated codes must be distributed to the sender and the receiver in a manner that ensures it is definitely only known to these two persons (requirement 4). With messengers, security is inevitably breached. Quantum physics again offers the ideal solution [forward].